Configuring SIP Message Policy Rules
The Message Policies table lets you configure up to
You can also enable the Message Policy to protect the device against incoming SIP messages with malicious signature patterns, which identify specific scanning tools used by attackers to search for SIP servers in a network. To configure Malicious Signatures, see Configuring Malicious Signatures.
Each Message Policy rule can be configured with the following:
| ■ | Maximum message length |
| ■ | Maximum header length |
| ■ | Maximum message body length |
| ■ | Maximum number of headers |
| ■ | Maximum number of bodies |
| ■ | Option to send 400 "Bad Request" response if message request is rejected |
| ■ | Blocklist and allowlist for defined methods (e.g., INVITE) |
| ■ | Blocklist and allowlist for defined bodies |
| ■ | Malicious Signatures |
The Message Policies table provides a default Message Policy called "Malicious Signature DB Protection" (Index 0), which is based only on Malicious Signatures and discards SIP messages identified with any of the signature patterns configured in the Malicious Signature table.
To apply a SIP Message Policy rule to calls, you need to assign it to the SIP Interface associated with the relevant IP Group (see Configuring SIP Interfaces).
The following procedure describes how to configure Message Policy rules through the Web interface. You can also configure it through ini file [MessagePolicy] or CLI (configure voip > message message-policy).
| ➢ | To configure SIP Message Policy rules: |
| 1. | Open the Message Policies table (Setup menu > Signaling & Media tab > Message Manipulation folder > Message Policies). |
| 2. | Click New; the following dialog box appears: |
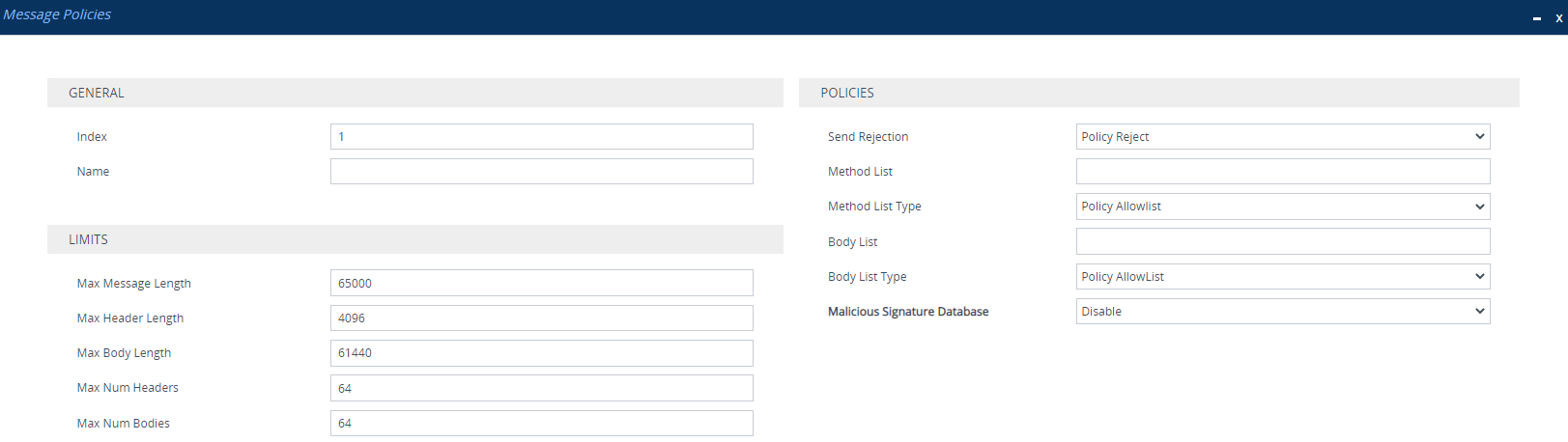
| 3. | Configure a Message Policy rule according to the parameters described in the table below. |
| 4. | Click Apply. |
Message Policies Table Parameter Descriptions
|
Parameter |
Description |
|||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| General | ||||||||||
|
'Index' [Index] |
Defines an index number for the new table row. Note: Each row must be configured with a unique index. |
|||||||||
|
'Name' name [Name] |
Defines a descriptive name, which is used when associating the row in other tables. The valid value is a string of up to 40 characters. Note:
|
|||||||||
|
Limits |
|
|||||||||
|
'Max Message Length' max-message-length [MaxMessageLength] |
Defines the maximum SIP message length. The valid value is up to 65,000 characters. The default is 65,000. |
|||||||||
|
'Max Header Length' max-header-length [MaxHeaderLength] |
Defines the maximum SIP header length. The valid value is up to 4,096 characters. The default is 4,096. |
|||||||||
|
'Max Body Length' max-body-length [MaxBodyLength] |
Defines the maximum SIP message body length. This is the value of the Content-Length header. The valid value is up to 61,440 characters. The default is 61,440. |
|||||||||
|
'Max Num Headers' max-num-headers [MaxNumHeaders] |
Defines the maximum number of SIP headers. The valid value is any number up to 64. The default is 64. Note: The device supports up to 20 SIP Record-Route headers that can be received in a SIP INVITE request or a 200 OK response. If it receives more than this, it responds with a SIP 513 'Message Too Large' response. |
|||||||||
|
'Max Num Bodies' max-num-bodies [MaxNumBodies] |
Defines the maximum number of bodies (e.g., SDP) in the SIP message. The valid value is any number up to 64. The default is 64. |
|||||||||
|
Policies |
|
|||||||||
|
'Send Rejection' send-rejection [SendRejection] |
Defines whether the device sends a SIP response if it rejects a message request due to the Message Policy. The default response code is SIP 400 "Bad Request". To configure a different response code, use the [MessagePolicyRejectResponseType] parameter.
|
|||||||||
|
SIP Method Blocklist-Allowlist Policy |
||||||||||
|
'Method List' method-list [MethodList] |
Defines the SIP methods for the blocklist or allowlist. Multiple methods are separated by a backslash (\), for example, "INVITE\BYE" (without quotations). The values are case-insensitive. |
|||||||||
|
'Method List Type' method-list-type [MethodListType] |
Defines the policy (blocklist or allowlist) for the SIP methods specified in the 'Method List' parameter (above).
|
|||||||||
|
SIP Body Blocklist-Allowlist Policy |
||||||||||
|
'Body List' body-list [BodyList] |
Defines the SIP body type (i.e., value of the Content-Type header) to blocklist or allowlist. For example, application/sdp. The values of the parameter are case-sensitive. |
|||||||||
|
'Body List Type' body-list-type [BodyListType] |
Defines the policy (blocklist or allowlist) for the SIP body specified in the 'Body List' parameter (above).
|
|||||||||
|
Malicious Signature |
||||||||||
|
'Malicious Signature Database' signature-db-enable [UseMaliciousSignatureDB] |
Enables the use of the Malicious Signature database (signature-based detection).
To configure Malicious Signatures, see Configuring Malicious Signatures. Note: The parameter is applicable only to the SBC application. |
|||||||||